Login Scenarios
Web Server Applications
Web Server Applications use the OAuth 2.0 Code Flow to obtain access tokens. The authorization sequence begins by the user agent being redirected to Saxo Bank's SSO system.
Saxo Bank's SSO system will authenticate the user and return an extended SSO token to the client application. This extended SSO token includes an OAuth authorization code.
At a later stage the Saxo Bank authorization servers will also prompt the user to accept/reject access for a particular application, which is standard behavior in a full Oauth 2.0 implementation.
The authorization code is then exchanged for an OpenAPI access token (and possibly an OpenAPI refresh token) by the application.
The web server may then call OpenAPI directly, or (which is most common) forward the access token to the user agent, which may then call OpenAPI.

When necessary, the client application may use the refresh token to obtain a new access token.
For details see the webserver application login documentation.
Native Applications
Installed applications use a flow very similar to the flow for web server applications. It assumes that the application has access to a system browser, or has a browser embedded as a web view.
An installed application must embed the application key and application secret in the application code, or it must reach back to it's own back-end server when completing the AuthCode-to-access token exchange. The client application is required to take reasonable appropriate measures to protect the application key and secret from discovery. Saxo Bank retains the right to revoke an application key/secret if it is found to have been disclosed and abused.
Again the authorization sequence begins by the user agent being redirected to Saxo Bank's SSO system.
Saxo Bank's SSO system will authenticate the user and return an extended SSO token to the client application. this extended SSO token includes an OAuth authorization code.
The authorization code is then exchanged for an OpenAPI access token (and possibly an OpenAPI refresh token) by the application.
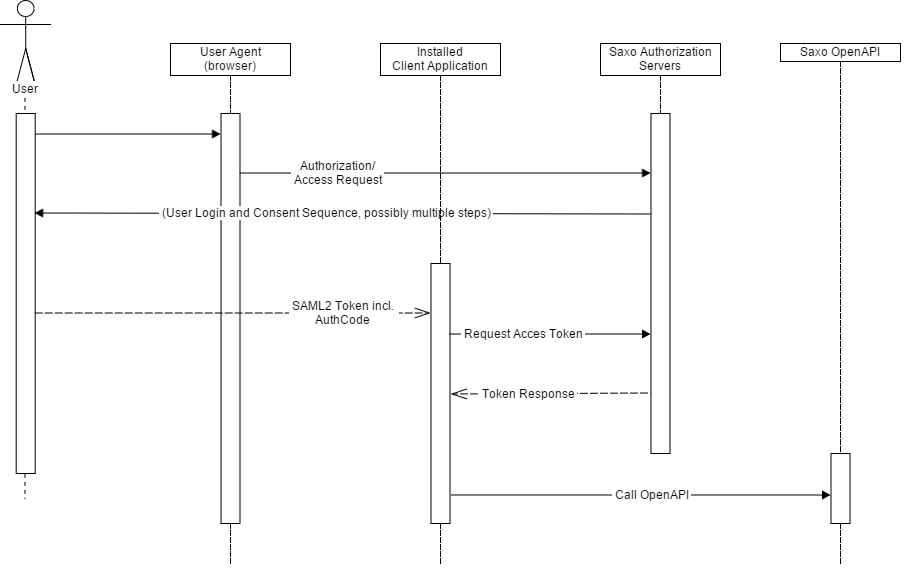
For details see the installed application login documentation.
Native Applications - Certificate Based Authentication
Server applications may use certificate based authentication to obtain an OpenAPI access token, without an actual user having to authenticate.
Currently Certificate-based Authentication is only available in our LIVE environment, and it is only available to select IBs and White Label Clients upon request.
In the certificated based authentication flow, the server application uses certificates to create a signed and encrypted request to the Saxo Bank authentication and authorization server. The request includes the the id of a user in the Saxo Bank system along with the application key and secret. The Saxo Bank authentication and authorization server will then provide an access token and optionally a refresh token in return.
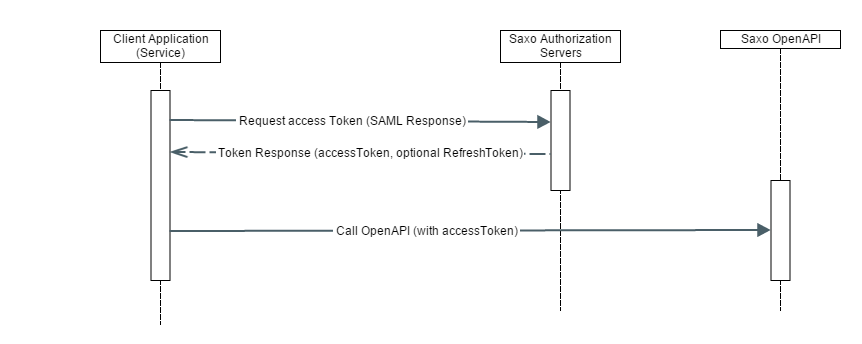
For details see the certificate based login documentation.